-
关注Ta
-
- 注册时间 2012-04-06
- 最后登录 2020-12-30
-
- 发帖288
- 在线146小时
- 精华1
- DB919
- 威望-3
- 保证金0
- 桃子0
- 鲜花0
- 鸡蛋0
-
访问TA的空间加好友用道具

|
 unpack ehsvc.rar[点击下载](5948 K) 下载次数:25 累计下载获得 DB 48 刀 unpack ehsvc.rar[点击下载](5948 K) 下载次数:25 累计下载获得 DB 48 刀不少人向我要新版过非法,我只能说我已经无能为力了。也没有心思做了,所以放一个今天脱掉TMD和还原过VM的ehsvc.dll送给大家研究。 还有两个区段未剔除,会弄的自己搞吧。 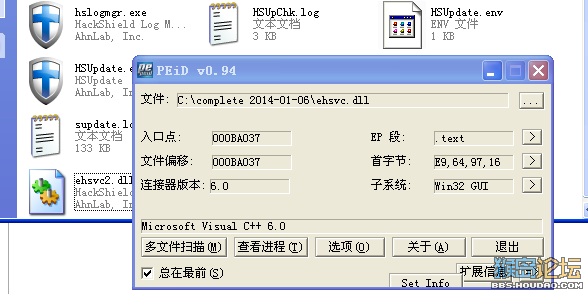 贴一段ehsvc对文件扫描的代码: 可以看到还原到这种程度效果可读还是很高的。
int __userpurge sub_1008B07A<eax>(int a1<eax>, int a2<ecx>, HANDLE hFile, LONG a4, int *a5)
{
DWORD v5; // eax@20
LONG v7; // [sp-18h] [bp-78h]@21
LONG v8; // [sp-14h] [bp-74h]@10
int v9; // [sp-10h] [bp-70h]@10
char v10; // [sp-Ch] [bp-6Ch]@1
int v11; // [sp+0h] [bp-60h]@1
char Buffer; // [sp+8h] [bp-58h]@11
int v13; // [sp+9h] [bp-57h]@11
__int16 v14; // [sp+Dh] [bp-53h]@11
char v15; // [sp+Fh] [bp-51h]@11
unsigned int i; // [sp+10h] [bp-50h]@14
char *v17; // [sp+14h] [bp-4Ch]@14
int v18; // [sp+18h] [bp-48h]@14
LONG lDistanceToMove; // [sp+1Ch] [bp-44h]@4
DWORD v20; // [sp+20h] [bp-40h]@4
LONG v21; // [sp+24h] [bp-3Ch]@4
struct _WIN_CERTIFICATE Certificateheader; // [sp+28h] [bp-38h]@4
DWORD NumberOfBytesRead; // [sp+34h] [bp-2Ch]@4
int v24; // [sp+38h] [bp-28h]@1
DWORD CertificateCount; // [sp+3Ch] [bp-24h]@1
DWORD v26; // [sp+40h] [bp-20h]@1
DWORD v27; // [sp+44h] [bp-1Ch]@1
char *v28; // [sp+48h] [bp-18h]@1
int v29; // [sp+50h] [bp-10h]@1
int (__cdecl *v30)(int, int, int); // [sp+54h] [bp-Ch]@1
int v31; // [sp+58h] [bp-8h]@1
int v32; // [sp+5Ch] [bp-4h]@1
v31 = (int)dword_1010BF50;
v30 = sub_100B67F0;
v29 = a1;
v28 = &v10;
v11 = a2;
v27 = 0;
v26 = 0;
*a5 = 0;
v32 = 0;
CertificateCount = 0;
v24 = 0;
v24 = ImageEnumerateCertificates(hFile, 0xFFu, &CertificateCount, 0, 0);
if ( v24 && CertificateCount )
{
v20 = 0;
lDistanceToMove = 0;
v21 = 0;
NumberOfBytesRead = 0;
Certificateheader.dwLength = 0;
*(_DWORD *)&Certificateheader.wRevision = 0;
*(_DWORD *)&Certificateheader.bCertificate[0] = 0;
v24 = ImageGetCertificateHeader(hFile, 0, &Certificateheader);
if ( v24 == 1 )
{
v21 = SetFilePointer(hFile, 0, 0, 1u);
if ( v21 == -1 )
{
v27 = GetLastError();
sub_10016310(
0,
dword_10123C30,
dword_10123C34,
dword_10123C38,
dword_10123C3C,
" Fail For Retrieving Current File Pos");
}
else
{
v26 = a4 - Certificateheader.dwLength;
lDistanceToMove = a4 - Certificateheader.dwLength - 8;
v20 = SetFilePointer(hFile, a4 - Certificateheader.dwLength - 8, 0, 0);
if ( v20 != -1 && v20 == lDistanceToMove )
{
Buffer = 0;
v13 = 0;
v14 = 0;
v15 = 0;
v24 = ReadFile(hFile, &Buffer, 8u, &NumberOfBytesRead, 0);
if ( v24 && NumberOfBytesRead == 8 )
{
v18 = 0;
v17 = &v15;
for ( i = 0; i < 8; ++i )
{
if ( *v17 )
{
v18 = 1;
break;
}
--v17;
}
if ( v18 == 1 )
{
*a5 = v26 - i;
v9 = *a5;
v8 = a4;
sub_10016310(
0,
dword_10123C30,
dword_10123C34,
dword_10123C38,
dword_10123C3C,
" Signed Info : dwFileSize (0x%x), dwOrgSize (0x%x)",
a4,
v9);
v5 = SetFilePointer(hFile, v21, 0, 0);
v20 = v5;
if ( v5 == -1 || v20 != v21 )
{
v27 = GetLastError();
v9 = v27;
sub_10016310(
0,
dword_10123C30,
dword_10123C34,
dword_10123C38,
dword_10123C3C,
" Fail For Resetting the File Pos To Prev Pos (Error : 0x%x)",
v27);
}
}
else
{
v27 = 1168;
v9 = i;
v8 = v26;
v7 = a4;
sub_10016310(
0,
dword_10123C30,
dword_10123C34,
dword_10123C38,
dword_10123C3C,
" Filtering Padded Value Failed (0x%x, 0x%x, 0x%x)",
a4,
v26,
i);
}
}
else
{
v27 = GetLastError();
v9 = v27;
sub_10016310(
0,
dword_10123C30,
dword_10123C34,
dword_10123C38,
dword_10123C3C,
" Fail For ReadFile (Error : 0x%x",
v27);
}
}
else
{
v27 = GetLastError();
v9 = v27;
v8 = lDistanceToMove;
sub_10016310(
0,
dword_10123C30,
dword_10123C34,
dword_10123C38,
dword_10123C3C,
" Fail For Moving File Pos to (0x%x) (Error : 0x%x)",
lDistanceToMove,
v27);
}
}
}
else
{
v27 = GetLastError();
}
}
else
{
*a5 = 0;
}
return v27;
}
signed int __cdecl sub_10089DEB(char a1)
{
signed int result; // eax@2
int v2; // [sp+4h] [bp-35Ch]@6
struct _WIN32_FIND_DATAA FindFileData; // [sp+8h] [bp-358h]@1
char v4; // [sp+148h] [bp-218h]@1
char v5; // [sp+149h] [bp-217h]@1
__int16 v6; // [sp+249h] [bp-117h]@1
char v7; // [sp+24Bh] [bp-115h]@1
char v8; // [sp+24Ch] [bp-114h]@1
char v9; // [sp+24Dh] [bp-113h]@1
char v10; // [sp+24Eh] [bp-112h]@1
char v11; // [sp+24Fh] [bp-111h]@1
char v12; // [sp+250h] [bp-110h]@3
char v13; // [sp+251h] [bp-10Fh]@3
char v14; // [sp+252h] [bp-10Eh]@3
char v15; // [sp+253h] [bp-10Dh]@3
char v16; // [sp+254h] [bp-10Ch]@3
HANDLE hFindFile; // [sp+258h] [bp-108h]@1
const CHAR FileName; // [sp+25Ch] [bp-104h]@1
v4 = 0;
memset(&v5, 0, 0x100u);
v6 = 0;
v7 = 0;
v8 = 37;
v9 = 115;
v10 = 42;
v11 = 0;
sub_10008850(&FileName, 260, &v8, a1);
hFindFile = FindFirstFileA(&FileName, &FindFileData);
if ( hFindFile == (HANDLE)-1 )
{
result = 0;
}
else
{
v12 = 37;
v13 = 115;
v14 = 37;
v15 = 115;
v16 = 0;
do
{
if ( !(FindFileData.dwFileAttributes & 0x10) )
{
v2 = 0;
sub_10086C60(FindFileData.cFileName, 260, &v2);
if ( v2 == 16 )
{
if ( sub_10089A75(FindFileData.cFileName) )
{
sub_10008850(&v4, 260, &v12, a1);
if ( sub_10089CC3(&v4) )
DeleteFileA(&v4);
}
}
}
}
while ( FindNextFileA(hFindFile, &FindFileData) );
if ( hFindFile != (HANDLE)-1 )
{
FindClose(hFindFile);
hFindFile = (HANDLE)-1;
}
result = 1;
}
return result;
}[ 此帖被小枫工作组在2014-01-06 15:13重新编辑 ]
|